Maester.dev is an open-source project which provides a framework to help maintain the security configuration of Microsoft cloud tenants (see https://maester.dev/) - and it's pretty great!
While the standard tests will get you to a very good tenant configuration, especially with regards to Conditional Access Policies, it is easy to better match the tests to your own needs.
Warning - this article assumes a basic understanding of Microsoft licensing with regards to conditional access!
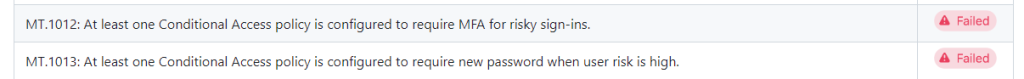
For example both tests MT.1012 and MT.1013, which deal with risk based conditional access policies (that need an entra P2 license) assume, that you have them in place for all of your users. Should you have a mixed environment with users with both an entra id P2 and an entra id P1 license, the test will fail, as you probably have only enabled this conditional access policy for your licensed users.
Short detour (we'll be back with Maester in a minute - I promise):
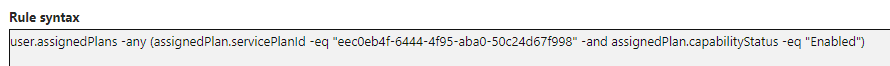
Now use that group to correctly scope your risk based conditional access policy.
And now back to maester!

Anyway, here we find that both tests check for all users:
if ( $policy.grantcontrols.builtincontrols -contains 'passwordChange' -and $policy.conditions.users.includeUsers -eq "All"
-and $policy.conditions.applications.includeApplications -eq "All" -and "high" -in $policy.conditions.userRiskLevels
)
Now that we finally have found out what these tests do, let's write a custom test that does not include the user requirement. We basically start out with the tests from Test-ConditionalAccessBaseline.Tests.ps1 and put our own test inline. For that I created a File ContosoEntraTests.ps1 in the Maester custom tests folder and added the test there:
BeforeDiscovery {
$EntraIDPlan = Get-MtLicenseInformation -Product "EntraID"
}
Describe "Conditional Access Baseline Policies Contoso" -Tag "CA", "Security", "All" -Skip:( $EntraIDPlan -eq "Free" ) {
It "MT.1012.Contoso: At least one Conditional Access policy is configured to require MFA for risky sign-ins. See https://maester.dev/docs/tests/MT.1012" -Skip:( $EntraIDPlan -eq "P1" ) {
$policies = Get-MtConditionalAccessPolicy | Where-Object { $_.state -eq "enabled" }
# Remove policies that require password change, as they are related to user risk and not MFA on signin
$policies = $policies | Where-Object { $_.grantcontrols.builtincontrols -notcontains 'passwordChange' }
$policiesResult = New-Object System.Collections.ArrayList
$result = $false
# Policy Check angepasst und "-and $policy.conditions.users.includeUsers -eq "All" `" entfernt, da nicht alle bei Contoso eine Entra ID P2 Lizenz besitzen
foreach ($policy in $policies) {
if ( ( $policy.grantcontrols.builtincontrols -contains 'mfa' `
-or $policy.grantcontrols.authenticationStrength.requirementsSatisfied -contains 'mfa' ) `
-and $policy.conditions.applications.includeApplications -eq "All" `
-and "high" -in $policy.conditions.signInRiskLevels `
-and "medium" -in $policy.conditions.signInRiskLevels ) {
$result = $true
$currentresult = $true
$policiesResult.Add($policy) | Out-Null
} else {
$currentresult = $false
}
Write-Verbose "$($policy.displayName) - $currentresult"
}
if ( $result ) {
$testResult = "The following conditional access policies require multi-factor authentication for risky sign-ins`n`n%TestResult%"
} else {
$testResult = "No conditional access policy requires multi-factor authentication for risky sign-ins."
}
Add-MtTestResultDetail -Result $testResult -GraphObjects $policiesResult -GraphObjectType ConditionalAccess
$result | Should -Be $true -Because "there is no policy that requires MFA for risky sign-ins"
}
#changed policy from require password change to block access and removed criterion that policy needs to include all users (not all users have entra id plan 2 license)
It "MT.1013.Contoso: At least one Conditional Access policy is configured to block access when user risk is high. See https://maester.dev/docs/tests/MT.1013" -Skip:( $EntraIDPlan -eq "P1" ){
$policies = Get-MtConditionalAccessPolicy | Where-Object { $_.state -eq "enabled" }
# Only check policies that have password change as a grant control
$policies = $policies | Where-Object { $_.grantcontrols.builtincontrols -contains 'passwordChange' }
$policiesResult = New-Object System.Collections.ArrayList
$result = $false
# Policy Check angepasst und "-and $policy.conditions.users.includeUsers -eq "All" `" entfernt, da nicht alle bei Contoso eine Entra ID P2 Lizenz besitzen
foreach ($policy in $policies) {
if ( $policy.grantcontrols.builtincontrols -contains 'passwordChange' `
-and $policy.conditions.applications.includeApplications -eq "All" `
-and "high" -in $policy.conditions.userRiskLevels `
) {
$result = $true
$currentresult = $true
$policiesResult.Add($policy) | Out-Null
} else {
$currentresult = $false
}
Write-Verbose "$($policy.displayName) - $currentresult"
}
if ( $result ) {
$testResult = "The following conditional access policies require password change for risky users`n`n%TestResult%"
} else {
$testResult = "No conditional access policy requires a password change for risky users."
}
Add-MtTestResultDetail -Result $testResult -GraphObjects $policiesResult -GraphObjectType ConditionalAccess
$result | Should -Be $true -Because "there is no policy that requires new password when user risk is high"
}
}
As you can see, both tests are more or less the same as the tests from the Maester module. But they do not check if the policy is in place for all users.
PS Big thanks to Fabian Bader, who pointed me into the right direction!